The “Russian Market” cybercrime market has emerged as one of the fashionable platforms for purchasing and promoting credentials stolen by data stealer malware.
Though {the marketplace} has been lively for roughly six years and have become comparatively fashionable by 2022, ReliaQuest reviews that the Russian Market has lately reached new heights. A part of this surge in recognition is as a result of takedown of the Genesis Market, which created a big vacuum within the subject.
Though the bulk (85%) of credentials offered on the Russian Market are “recycled” from current sources, it has nonetheless received huge cybercrime audiences due to its broad choice of objects of sale and availability of logs at costs as little as $2.
An infostealer log is often a textual content file, or a number of recordsdata, created by infostealer malware that incorporates the account passwords, session cookies, bank card information, cryptocurrency pockets information, and system profiling information stolen from an contaminated machine.
Every log can include dozens and even 1000’s of credentials, so the entire variety of stolen credentials may very well be a whole bunch of hundreds of thousands or extra. As soon as collected, the logs are uploaded again to an attacker’s server, the place they’re collected to be used in additional malicious exercise or offered on marketplaces just like the Russian Market.
Supply: ReliaQuest
Infostealers have grow to be an immensely fashionable device for risk actors, with many campaigns now concentrating on the enterprise to steal session cookies and company credentials.
ReliaQuest says that is mirrored within the Russian Market, with 61% of the stolen logs containing SaaS credentials from platforms like Google Workspace, Zoom, and Salesforce. Additionally, 77% of the logs included SSO (Single Signal-On) credentials.
“Compromised cloud accounts afford attackers entry to vital methods and current the right alternative to steal delicate information,” explains the researchers.
Lumma falters, Acreed rises
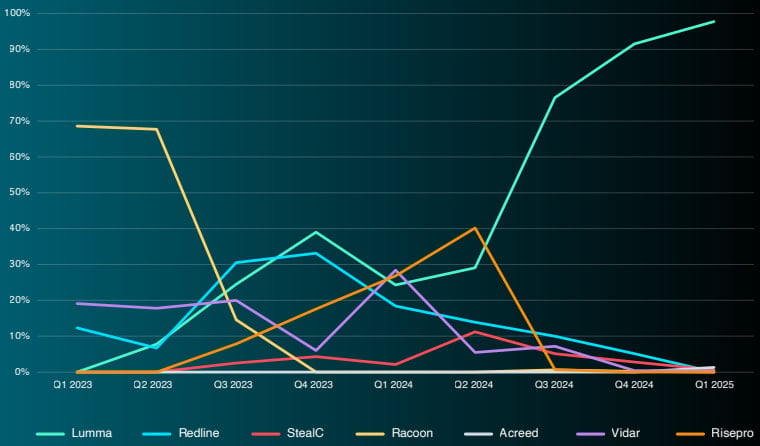
ReliaQuest analyzed over 1.6 million posts on the Russian Market to graph the rise and fall in recognition of particular info-stealing malware.
Till lately, most logs had been stolen by Lumma stealer, which accounts for 92% of all credential logs offered on the Russian Market.
Supply: ReliaQuest
Lumma dominated the market after the collapse of Raccoon Stealer, following legislation enforcement motion. Nonetheless, the identical destiny may very well be unfolding for Lumma, as its operations had been lately disrupted by a worldwide legislation enforcement operation the place 2,300 domains had been seized.
The long-term outcomes of this operation stay unclear, and Test Level reported that Lumma’s builders are at present trying to rebuild and restart their cybercrime operations.
Within the meantime, ReliaQuests reviews seeing a sudden rise of a brand new infostealer named Acreed, which is quickly gaining traction following the takedown of Lumma.
Acreed’s swift ascent within the Russian Market is mirrored within the over 4,000 logs uploaded inside its first week of operations, in keeping with Webz.
Acreed is not completely different from a typical info-stealer concerning the knowledge it targets, which incorporates information saved in Chrome, Firefox, and their numerous derivatives, together with passwords, cookies, cryptocurrency wallets, and bank card particulars.
Information-stealers are infecting customers through phishing emails, “ClickFix” assaults, malvertising for premium software program, and YouTube or TikTok movies. So, vigilance and good software program obtain practices are advisable to keep away from this widespread danger.

Handbook patching is outdated. It is gradual, error-prone, and hard to scale.
Be a part of Kandji + Tines on June 4 to see why previous strategies fall brief. See real-world examples of how fashionable groups use automation to patch quicker, lower danger, keep compliant, and skip the complicated scripts.

