Telephones have change into an indispensable a part of day by day life in Nigeria, serving as important instruments for communication, social interplay, and enterprise operations. When a telephone is misplaced or somebody’s security is in danger, figuring out learn how to monitor a telephone quantity turns into essential.
Monitoring a telephone in Nigeria isn’t one thing you are able to do freely; there are strict privateness legal guidelines to guard folks. In 2025, monitoring is barely permitted in particular conditions. For instance, you should use apps like Google Discover My System or Apple’s Discover My to find your misplaced telephone. Nevertheless, monitoring another person’s machine, even for good causes, requires authorized authorisation or their express consent. This makes it difficult for most individuals to determine learn how to monitor a telephone quantity legally in Nigeria. One regulation you need to be conscious of is the Nigerian Knowledge Safety Act (NDPA) 2023. It was signed into regulation on June 12, 2023, and establishes clear guidelines relating to the dealing with of non-public info. It additionally led to the institution of the Nigerian Knowledge Safety Fee (NDPC), which ensures that these guidelines are adhered to.
Which means that utilizing shady apps or counting on methods to trace telephones with out permission is now not a gray space; it’s merely unlawful.
Right here’s a desk that can assist you perceive the principle monitoring choices accessible in Nigeria in 2025:
How regulation enforcement tracks telephones in Nigeria
In case your telephone will get stolen or there’s a felony investigation, there are official methods telephones may be tracked in Nigeria, however solely by the best authorities. These strategies are authorized, dependable, and supported by strong methods designed to make sure nationwide safety and public security.
1. IMEI monitoring:
Each cell phone has a novel 15-digit code, often called the IMEI (Worldwide Cellular Tools Id). It’s like a fingerprint on your telephone. Once you make a name or ship a textual content, your telephone shares its IMEI quantity with the community. This allows monitoring of the machine, even when the SIM card is changed.
However right here’s the catch: solely police and accredited safety companies are allowed to trace telephones utilizing IMEI numbers. You may’t monitor somebody’s telephone your self utilizing their IMEI; it’s in opposition to the regulation. So whilst you can’t use IMEI personally, it’s nonetheless a sound technique when asking learn how to monitor a telephone quantity by way of official means.
In case your telephone goes lacking, the best factor to do is to report it to the police. You’ll want to provide:
- Your IMEI quantity (dial *#06# in your telephone to search out it)
- A proper police report
- Your contact quantity and an e mail tackle
The police can then start monitoring by way of authorized channels.
The Nigerian Communication Fee (NCC) has additionally launched a System Administration System (DMS). This technique connects Nigerian telephone data to world IMEI databases. In case your telephone is blacklisted, it turns into ineffective on all networks within the nation, this helps cut back theft and blocks the resale of stolen telephones.
2. How telcos assist police monitor telephones
Cellular community suppliers, reminiscent of MTN, Airtel, Glo, and 9mobile, additionally play a major position. By regulation, they have to work with regulation enforcement to assist monitor felony exercise and shield nationwide security.
These corporations present what is known as name information, together with particulars reminiscent of who known as whom, when, and the place. In lots of instances, this information may be accessed by the police with written approval from a senior officer, even with no courtroom order.
Authorities officers have made it clear: telcos should cooperate. In the event that they don’t, they are often penalised.
Nonetheless, there are challenges. Audits by the NCC have discovered that some suppliers didn’t totally observe SIM registration and information safety guidelines. Which means that whereas the regulation is in place, correct enforcement nonetheless wants enchancment to make sure the monitoring course of stays dependable.
3. NIN and SIM registration:
You’ve in all probability heard of the NIN-SIM linkage. This implies each telephone quantity have to be tied to a Nationwide Id Quantity (NIN). It’s not optionally available.
For the reason that regulation began, over 153 million SIM playing cards have been linked to NINs in Nigeria. The aim is to verify each SIM card is related to an actual individual. This helps safety companies hint telephone exercise again to people. This linkage can also be very important for authorities when figuring out learn how to monitor a telephone quantity tied to suspicious or felony exercise.
For instance, if somebody makes use of their telephone throughout against the law, the police can determine the proprietor by way of the Nationwide Id Quantity (NIN) related to the SIM card. Telecom suppliers like MTN even provide on-line portals that can help you test in case your line is linked appropriately.
Once you mix SIM registration with the DMS system that tracks IMEI numbers, the federal government will get a a lot clearer view of who’s utilizing every telephone, and the place.
4. NCC’s System Administration System (DMS):
The System Administration System (DMS) is a instrument created by the NCC to regulate and monitor all telephones in Nigeria. It collects the IMEI numbers of each machine related to a Nigerian community and checks them in opposition to worldwide databases.
The aim? To cease faux or stolen telephones from working, shield telephone customers, and assist police monitor down telephones utilized in crimes.
As soon as a telephone’s IMEI is reported as stolen, it’s added to a blacklist shared with all cell networks. This implies even when somebody modifications the SIM, the telephone received’t work.
The DMS additionally helps:
- Cut back telephone theft and kidnappings
- Cease unlawful telephones from coming into the market
- Defend customers from shopping for blacklisted gadgets
However there’s a priority: the system is highly effective, and there isn’t a lot public info on how lengthy information is saved or how your privateness is protected. Though it enhances security, it additionally opens the door to potential overreach.
5. Cell tower triangulation:
One other technique regulation enforcement can use to trace telephones is cell tower triangulation. Each time your telephone is on, it connects with the closest cell towers. By checking which towers your telephone talked to and the way robust the sign was, authorities can work out roughly the place the telephone is.
If the telephone connects to at the least three towers concurrently, they’ll triangulate your place, usually with an accuracy of about 70–80%. Add GPS monitoring, and that jumps to about 90%.
This technique helps police get each:
- Actual-time location information (the place the telephone is correct now)
- Historic information (the place the telephone has been)
Telecom corporations retailer this data, and police can entry it by way of authorized requests or courtroom orders. As a result of each registered SIM is tied to an individual’s NIN, it turns into simpler to know who used the telephone and when.
This technique is trusted worldwide and stays one of the crucial exact methods on learn how to monitor a telephone quantity, to find suspects and remedy crimes.
Easy methods to monitor a telephone quantity the best approach
You don’t must undergo the police simply to discover a misplaced telephone, to control your little one’s machine or learn to monitor a telephone quantity. When you’re attempting to trace your telephone or have the clear permission of a member of the family, there are trusted apps that may assist. These apps are constructed into your telephone or may be downloaded from app shops.
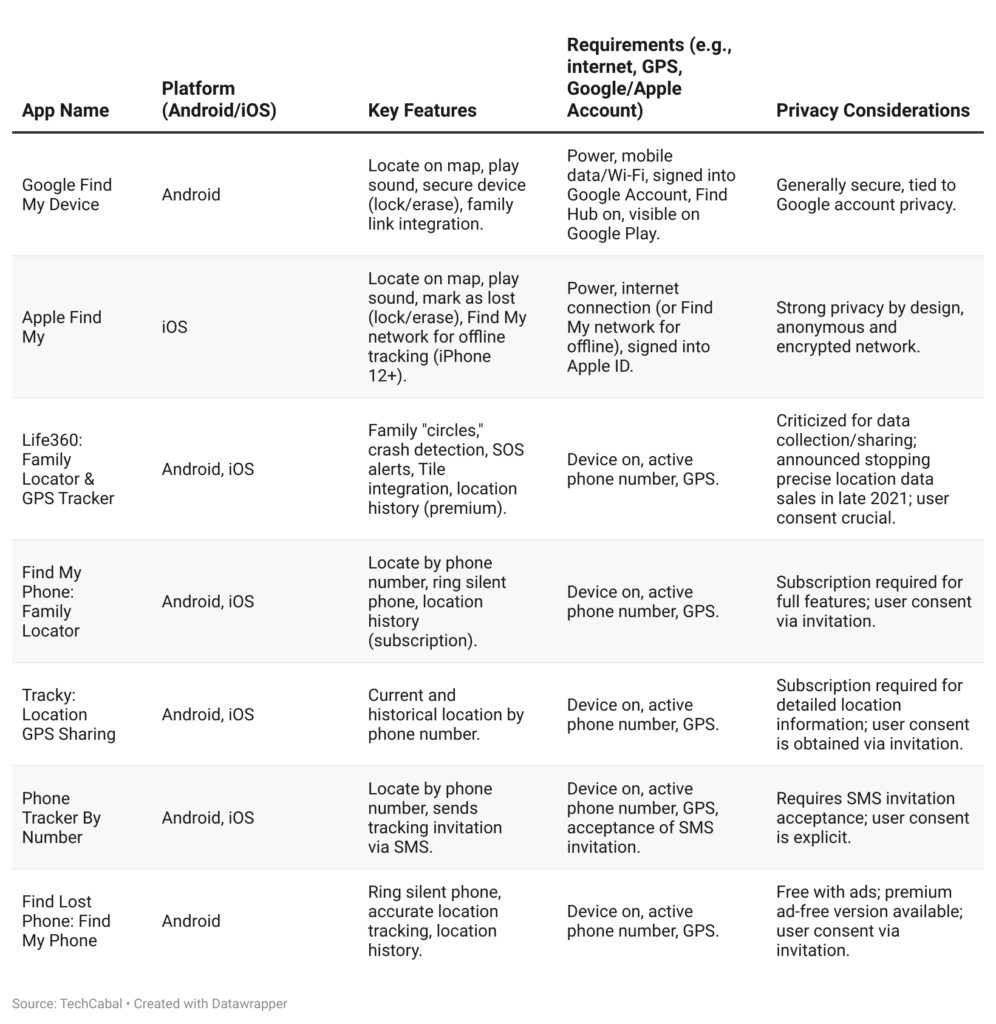
1. Google Discover My System (for Android customers)
When you use an Android telephone, Google Discover My System is without doubt one of the best methods to trace it. When you add your Google account to your telephone, this characteristic is robotically turned on (except you’ve disabled it).
With it, you may:
- See your telephone on a map
- Make it ring loudly, even when it’s on silent
- Lock it remotely or present a message on the display screen
- Erase every thing on it when you can’t get it again
However for this to work, your telephone have to be:
- Turned on
- Linked to Wi-Fi or cell information
- Signed into your Google account
- Seen on Google Play
- Location companies are turned on
When you use Household Hyperlink to handle your little one’s machine, their telephone can even present up robotically in your Discover My System app. This makes it simpler to handle household security.
2. Apple Discover My (for iPhone, iPad, and Mac customers)
For iPhone and different Apple gadgets, Discover My works equally. You may:
- Discover the telephone on a map
- Play a sound
- Lock or erase it
Apple goes a step additional. With newer iPhones (iPhone 12 and up), you may nonetheless see the place the telephone was, even when it’s offline or turned off. It does this utilizing close by Apple gadgets within the community to ship the placement.
Nevertheless, this characteristic doesn’t work on older iPhones. And if the telephone is off or lacks a sign, even newer iPhones could not replace their location till they arrive on-line once more.
3. Third-Get together monitoring apps
There are additionally apps you may obtain from the Google Play Retailer or Apple App Retailer to trace telephones with consent. These apps are widespread for households or small teams who conform to share their areas. They’re a easy and authorized reply to the query of learn how to monitor a telephone quantity with out breaking Nigeria’s privateness legal guidelines.
Listed here are just a few examples:
- Life360: Tracks telephones inside a non-public group (known as a Circle). It additionally affords alerts, crash detection, and SOS options. Works provided that GPS and information are on.
- Discover My Cellphone: Household Locator: Allows you to discover a machine by telephone quantity. Some options require a paid subscription.
- Tracky: Retains monitor of previous areas and shares real-time updates. Works effectively when the telephone has a great sign.
- Cellphone Tracker By Quantity: Sends a request to the telephone you’re monitoring. As soon as they settle for it, you may see their location.
- Discover Misplaced Cellphone: Discover My Cellphone: Helpful in case your telephone is close by. It might trigger the telephone to ring loudly, even when it’s in silent mode.
It’s necessary to notice that these apps solely work with consent. You may’t set up or use them secretly. Doing so is in opposition to the regulation and violates Nigeria’s Knowledge Safety Act (NDPA 2023).
Desk: Comparability of authentic private monitoring apps
Cellphone monitoring myths you shouldn’t fall for
There’s loads of confusion round telephone monitoring in Nigeria. Some folks attempt shortcuts that both don’t work, are unlawful, or put them prone to scams. Let’s break down the most typical myths and what it is advisable be careful for.
1. You may monitor a telephone utilizing USSD codes
You will have seen messages or movies claiming that dialling a particular USSD code (like *123#) will help you monitor a telephone. That is false.
USSD codes are brief numbers you utilize to test airtime, purchase information, recharge your line, or make cell transfers. For instance:
- MTN: *310# to test steadiness, *312# to purchase information
- OPay: *955# to test steadiness, 9551# to ship cash
None of those codes is supposed for monitoring telephones. They provide help to discuss to your community supplier’s system, not find a lacking machine. Believing in any other case wastes time and should expose you to shady web sites or apps that don’t work.
2. Common folks can use Stingray gadgets
Stingray gadgets (also called IMSI catchers) are instruments utilized by federal safety companies to trace folks underneath investigation. They work by pretending to be a cell tower and tricking telephones close by into connecting.
As soon as related, the Stingray can acquire location information, name data, and extra. However this tech is:
- Unlawful for personal use
- Costly and exhausting to get
- Solely accredited for police or nationwide safety companies, and normally requires a courtroom order.
Even when utilized by officers, Stingrays include privateness considerations. They don’t simply monitor the goal; they’ll decide up information from any telephone close by, together with yours. That’s why their use is controversial and intently watched in lots of nations, together with Nigeria.
If anybody affords you this service on-line, keep away from it. It’s seemingly a rip-off, or worse, an unlawful setup.
3. Cellphone restore outlets can monitor telephones
Restore outlets in locations like Pc Village in Lagos repair telephones; they don’t monitor them.
They will help with:
- Changing damaged screens
- Fixing charging points
- Recovering recordsdata from a broken telephone
Nevertheless, they lack entry to networks and regulation enforcement databases. In case your telephone is misplaced or stolen, they’ll’t provide help to hint it. At finest, they’ll test if somebody brings in your stolen machine for repairs.
Pc Village has made an effort to enhance its picture. Distributors now register with ID playing cards, and security measures like CCTV and emergency alert methods are being put in. However once more, these are crime prevention instruments, not monitoring instruments.
4. SIM cloning helps you monitor a telephone
SIM cloning means copying somebody’s SIM card to achieve entry to their calls and messages. This isn’t solely unlawful but in addition a severe cybercrime.
The Nigerian Communications Fee (NCC) has made it very exhausting to interchange a SIM card with out proof of possession. When you lose your SIM, you’ll must:
- Present ceaselessly known as numbers
- Deliver a sound ID and a passport picture
- Submit an affidavit and proof of recharge
- Get your image taken by the telco
Making an attempt to clone a SIM or asking somebody to do it for monitoring is a felony offence. It might result in jail time, heavy fines, or each, and it opens the door to different crimes, reminiscent of id theft and fraud.
So if somebody affords to clone a SIM so you may “see their messages” or “monitor their telephone,” stroll away.
5. You may pay somebody on social media to trace a telephone
Scammers usually make the most of folks determined to recuperate a misplaced or stolen telephone. They promise monitoring companies on-line, then disappear along with your cash or private data.
Some even fake to be mates on-line, acquire your belief, after which trick you into sending personal info or pictures. Later, they blackmail victims utilizing threats or faux screenshots.
That is known as:
- Romance scams (faux relationships used to steal cash)
- Sextortion scams (threats made utilizing intimate pictures)
The FBI has even despatched groups to Nigeria to cope with this concern, particularly after instances the place victims have been pushed to the sting. In some heartbreaking instances, victims took their very own lives.
Right here’s learn how to shield your self:
- By no means ship cash to anybody claiming they’ll monitor a telephone on-line
- Keep away from affords that sound “too good to be true.”
- Don’t share private data with strangers, even when they appear pleasant
- When you’ve already been focused, report it to the FBI’s IC3 (Web Crime Grievance Centre) or a trusted cybersecurity agency
Closing ideas: Two authorized methods to trace a telephone
There are solely two trusted paths to observe:
1. Undergo regulation enforcement
In case your telephone is stolen otherwise you’re serving to somebody recuperate theirs, report it to the police. They’ll monitor it utilizing the telephone’s IMEI quantity, with help from community suppliers reminiscent of MTN, Airtel, Glo, and 9mobile.
Different instruments that assist regulation enforcement embrace:
- SIM-NIN linkage (which ties telephone numbers to actual identities)
- The NCC’s System Administration System (DMS) that blacklists stolen telephones
- Cell tower triangulation to search out telephone areas
These strategies are solely accessible to authorised companies, not personal people.
2. Use private monitoring instruments
When you’ve misplaced your telephone or wish to preserve tabs on a member of the family with their permission, you should use:
- Google Discover My System (for Android)
- Apple Discover My (for iPhones and different Apple gadgets)
- Third-party apps like Life360, solely when everybody concerned provides clear consent
Take note: these instruments solely work if the telephone is:
- Turned on
- Linked to cell information or Wi-Fi
- Has location companies enabled
If a thief turns off the telephone, removes the SIM, or resets it, these instruments will cease working.
Don’t take unlawful shortcuts
Keep away from something that feels like a secret hack or backdoor. This consists of:
- SIM cloning
- Stingray or IMSI catcher gadgets
- Paying somebody on social media to “provide help to monitor” a telephone
These strategies are unlawful, unsafe, and infrequently scams. You might lose cash, fall sufferer to blackmail, and even break the regulation with out figuring out it.

